A secure meeting experience means that you should have full control over who has access (to your meetings) and when they have access – always.
In a world where some of our most important conversations happen on video, it’s paramount to ensure that the right people are in the right meeting at the right time. This requires taking steps to prevent unauthorized access, data breaches, and eavesdropping.
And simply adding a password to protect your meeting isn’t going to cut it anymore.
What is the actual risk of unauthorized access?
Today, hackers can exploit weaknesses in video conferencing software to gain access to meetings, from which they can potentially glean confidential or valuable information. The motivation may also be to disrupt and/or prevent communication or cause reputational harm.
A post-Covid IBM survey of (US) companies that recently experienced a data breach reported that the average cost of that breach was as much as $4.5 million, and 83% of the survey respondents stated that they experienced more than one attack. This IBM report concluded that as the number of people working remotely rises, so too will the number of data breaches.
Right people
At Pexip, we see “authentication” as the first line of defense for your video meeting. This is a method of validation to ensure that only authorized users can access the video conferencing system. A multi-factor authentication protocol should be standard practice for any security conscious organization, which means that access to the meeting requires a combination of identification methods – such as a password plus a code sent to another device, or a code plus biometric verification, for example.
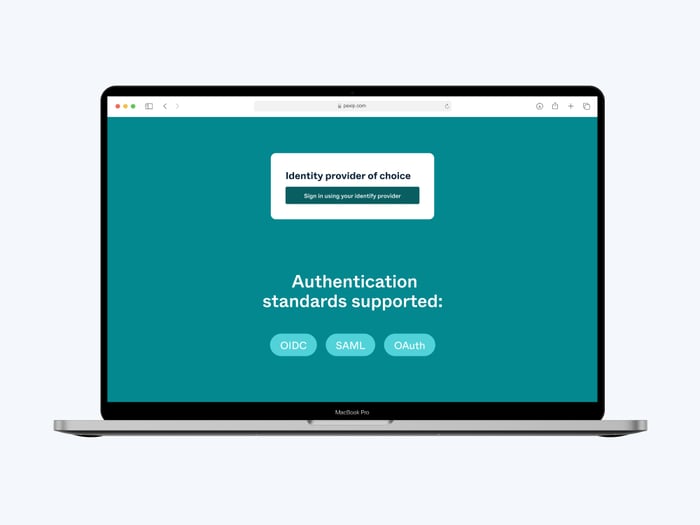
For organizations that want to go above and beyond multi-factor authentication, working with an identity provider can deliver an extra layer of authentication control, such as verification through a digital identity service, to support complex identity management requirements. It’s important to ensure that your video conferencing systems support identity services and standards.
Right meeting, right time
Once you’ve verified that the meeting attendee is who they say they are, the next level of control is about ensuring that they are in the right meeting at the right time. This is what we call “access control”, which is all about directing and/or restricting the user in the video conferencing system. There are two primary ways to define a person’s rights when it comes to meeting access:
The first way is based on their role in the organization.
Perhaps you have a meeting with the Board that only executive management and board members should have access to, or a meeting about a re-organization solely for the ears of the HR staff. This type of access control is called “role-based access control” (RBAC).
The second way is based on attributes of either the user, their location, the network they are on, or even the device they are using to join the meeting.
An organization may want to restrict access to a user joining from a public network, for example, or someone joining from outside the country. This is called “attribute-based access control” (ABAC). Organizations can continuously manage and enforce their video meeting access policies using an external policy engine. These are servers that evaluate requests to join meetings based on predefined policies – which could be role or attribute based, or even a combination, such as a person at a certain military rank who can only access the meeting during one hour of the day.
This method enables real-time decisions about who can join a meeting, at what time, and even so far as what they are allowed to do in that meeting – such as whether they can only listen and/or if their microphone can be enabled.
Control and confidence
Authentication and access control play a vital role in secure meetings, giving users the control and confidence they need to ensure that the right people are in the right meeting at the right time.
At Pexip, we work with some of the most security conscious organizations in the world, helping them build a robust defense around their most confidential communications. Our platform supports customizable access controls, allowing for specially designed security policies.
Reach out to learn more about how we are protecting your critical video meetings.