Secure by Design.
Secure by Default.
We are committed to building security into everything we do.
By integrating proactive, risk-based security measures from the outset, we aim to protect our organization, partners, and customers from evolving threats and vulnerabilities.
Pexip's security practices
These are our tasks that form part of our development process and applies to all development within Pexip.
Security by Default, Privacy Always
Pexip incorporates security into our product design from planning through development, implementation, and sustainment. Too many companies and products attempt to “bolt on” security after the initial product design, inevitably resulting in security breaches and data loss. At Pexip, protecting your organisational and individual privacy is our primary mission.
Defence in Depth
Defence in Depth refers to having multiple layers of interoperational security. Pexip’s software design process incorporates the Defense in Depth approach to ensure potential vulnerabilities in one functional area do not impact the overall risk to your organisation’s data.
Least Privilege
The principle of Least Privilege states that users and devices should only be given the minimum amount of system, application, and data access necessary to perform their job. In our business as in our products, Pexip defines and assigns roles and data access constraints to ensure that only those with a Need to Know have access to application, business, or customer data and metadata.
Supply Chain Risk Management
Supply chain risk management (SCRM) aims to minimize the impact of upstream dependencies on the overall security of products and services. At Pexip, our SCRM approach recognizes that we are both a consumer and a producer of supply chain risk. We manage our upstream software dependencies in accordance with our SDLC, and we aim to provide our customers with the security knowledge and artifacts necessary for their SCRM policies and processes.
Threat Modelling
Threat modelling is the process of considering the potential risks and threats of product design and determining how those issues can be addressed. By incorporating threat modelling at the planning stage of development, Pexip’s software lifecycle ensures that security and privacy concerns are included in product planning and architectural design, not just added as a “layer” or feature capability as an afterthought.
Secure Software Development Life Cycle (SSDLC)
Security features and capabilities
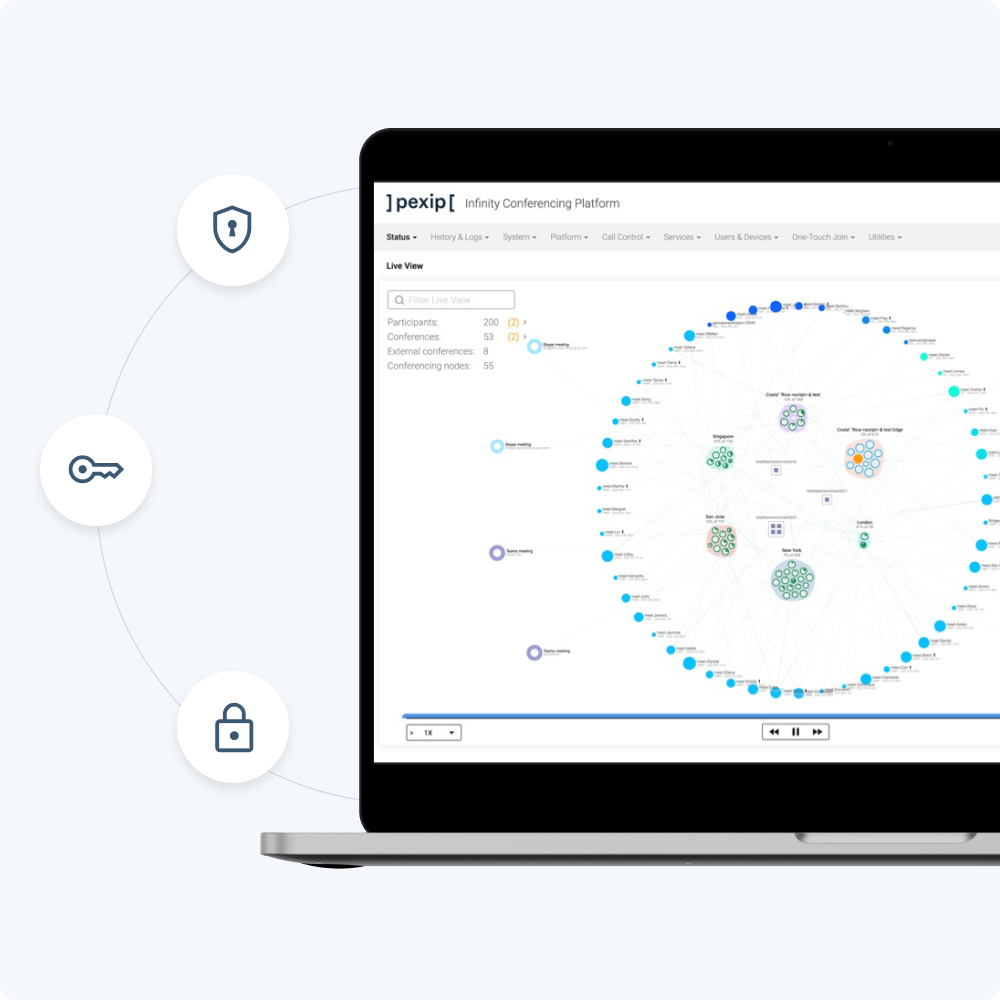
Pexip Infinity
Infinity powers Secure Meetings, Pexip Video Platform, and Pexip Connect Standard (self-hosted deployment).
The self-hosted solution supports the industry standards for communication encryption for end-user devices, ensuring that communication is secure and kept private even if it crosses the internet.
- Private deployments befitting your specific hosting architecture
- Attribute-Based Access Control (ABAC) support
- Participant-specific security protocols
- Global and local policy compliance engine
- API support for customer-developed security policy stack
- FIPS-compliant cryptographic algorithms
- Application and Session Intrusion Detection and Prevention
- Host-based File Integrity Monitoring (FIM)
- Purpose-built hardened operating system
- NIST- and ISO-compliant auditing and logging
Pexip Service
The Service enables secure calling and interoperability powering Pexip Connect (software-as-a-service). The Service supports the industry standards for communication encryption for end-user devices, ensuring that communication is secure and kept private even if it crosses the internet.
- Highly redundant, globally accessible and geographically dispersed architecture
- Dedicated operations teams providing continuous monitoring
- Monitoring and metrics provide visibility into your organisation’s communication needs
- Ideal companion to self-hosted deployments as part of your Business Continuity and Disaster planning
- GDPR compliant and CSA Star Level 1 certified
- Hosted in SOC2 compliant datacentres
- Operated in accordance with the requirements of Pexip’s ISO certifications:
- ISO 27001 with additional controls for ISO 27017 shared security responsibilities, ISO 27018 responsibilities for processors of personal data (PII)
- ISO 27701 Privacy Information Management System for the development, provision, management and delivery of collaboration as a service with the role of PII processor.

Pexip Government Cloud
Pexip Government Cloud (PGC) is Pexip’s FedRAMP and StateRAMP Authorized Government Community Cloud service offering for US customers. PGC supports US federal, state and local, and associated organizations such as government contractors, academia, or public-private consortia.
- FedRAMP-Authorized Moderate SaaS
- Microsoft (MS) CVI and Video Meeting Room (VMR) support
- High Availability deployment using MS Azure
- Developed with Pexip’s Infinity video engine
- FIPS 140-3 compliant
- Customer-specific call policies and Dial Plans
- Zero Trust-compliant device, user, and data authorization
- Customer-owned SAML identity management
- Federally-compliant Continuous Monitoring and reporting

Pexip VPaaS
- Geo-fenced services allowing for isolation of data into a specifically desired region
- No access to personally identifiable information (PII)
- Fully API and SDK driven service, allowing organizations to build their own call flow policies
- Deployed as a Zero Trust Architecture (ZTA)
- Application and Session Intrusion Detection and Prevention
- GDPR compliant
- Enables customers to achieve HIPAA compliance
Pexip Infinity
Infinity powers Secure Meetings, Pexip Video Platform, and Pexip Connect Standard (self-hosted deployment).
The self-hosted solution supports the industry standards for communication encryption for end-user devices, ensuring that communication is secure and kept private even if it crosses the internet.
- Private deployments befitting your specific hosting architecture
- Attribute-Based Access Control (ABAC) support
- Participant-specific security protocols
- Global and local policy compliance engine
- API support for customer-developed security policy stack
- FIPS-compliant cryptographic algorithms
- Application and Session Intrusion Detection and Prevention
- Host-based File Integrity Monitoring (FIM)
- Purpose-built hardened operating system
- NIST- and ISO-compliant auditing and logging

Pexip Service
The Service enables secure calling and interoperability powering Pexip Connect (software-as-a-service). The Service supports the industry standards for communication encryption for end-user devices, ensuring that communication is secure and kept private even if it crosses the internet.
- Highly redundant, globally accessible and geographically dispersed architecture
- Dedicated operations teams providing continuous monitoring
- Monitoring and metrics provide visibility into your organisation’s communication needs
- Ideal companion to self-hosted deployments as part of your Business Continuity and Disaster planning
- GDPR compliant and CSA Star Level 1 certified
- Hosted in SOC2 compliant datacentres
- Operated in accordance with the requirements of Pexip’s ISO certifications:
- ISO 27001 with additional controls for ISO 27017 shared security responsibilities, ISO 27018 responsibilities for processors of personal data (PII)
- ISO 27701 Privacy Information Management System for the development, provision, management and delivery of collaboration as a service with the role of PII processor.

Pexip Government Cloud
Pexip Government Cloud (PGC) is Pexip’s FedRAMP and StateRAMP Authorized Government Community Cloud service offering for US customers. PGC supports US federal, state and local, and associated organizations such as government contractors, academia, or public-private consortia.
- FedRAMP-Authorized Moderate SaaS
- Microsoft (MS) CVI and Video Meeting Room (VMR) support
- High Availability deployment using MS Azure
- Developed with Pexip’s Infinity video engine
- FIPS 140-3 compliant
- Customer-specific call policies and Dial Plans
- Zero Trust-compliant device, user, and data authorization
- Customer-owned SAML identity management
- Federally-compliant Continuous Monitoring and reporting

Pexip VPaaS
- Geo-fenced services allowing for isolation of data into a specifically desired region
- No access to personally identifiable information (PII)
- Fully API and SDK driven service, allowing organizations to build their own call flow policies
- Deployed as a Zero Trust Architecture (ZTA)
- Application and Session Intrusion Detection and Prevention
- GDPR compliant
- Enables customers to achieve HIPAA compliance

Recent CVEs

